Cloud migration involves relocating applications, data and other business processes to a cloud computing environment. This allows organizations to take advantage of the scalability, cost-effectiveness, and agility offered by cloud computing. However, with the increasing adoption of cloud computing, organizations must also consider the potential security risks associated with migrating to the cloud.
Introduction to Data Security Posture Management
Data security posture management (DSPM) is a key component of cloud security that helps organizations to maintain a secure posture while using the cloud. This involves ensuring that the data stored in the cloud is secure and that measures have been implemented to block unauthorized data access. This article discusses how data security posture management can be used to mitigate the risks associated with cloud migration.
Why Is Data Security Posture Management Important for Cloud Migration?
Data security posture management is important for cloud migration because it helps organizations ensure that the data stored in the cloud is secure. When migrating to the cloud, organizations must consider the potential risks, such as data breaches, loss of data, and unauthorized access to the data. Data security posture management helps organizations minimize these risks by ensuring that the stored data in the cloud is safe and that access controls are in place to prevent unauthorized data access.
How Does Data Security Posture Management Mitigate the Risks of Cloud Migration?
Encryption of Data
Encryption is a key component of data security posture management that helps organizations to protect the data stored in the cloud. Encryption helps ensure that data stored in the cloud is secure and cannot be accessed by unauthorized individuals. Encryption also helps prevent data breaches because even if a hacker successfully accesses the data, they will not be able to read it. Organizations can use encryption to secure both data at rest and data in transit, which helps to ensure that the data is secure at all times.
Access Controls
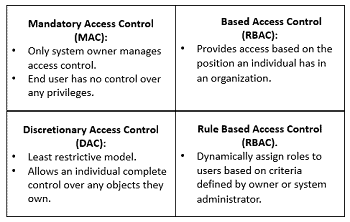
Access control is another critical component of data security posture management that help organizations prevent unauthorized access to data stored in the cloud. Access controls can include authentication and authorization mechanisms and role-based access controls that allow only authorized individuals to access the data.
Monitoring and Auditing
Monitoring and auditing are critical components of data security posture management that help organizations to ensure that the data stored in the cloud is secure. Monitoring helps organizations detect any security incidents that occur, while auditing helps organizations track changes to the data and ensure that the access controls are functioning properly. Organizations should also implement continuous monitoring and regular auditing to ensure that the data stored in the cloud remains secure.
Risk Assessment
Data security posture management also involves conducting a risk assessment to identify the potential risks associated with cloud migration. This helps organizations to understand the potential risks associated with migration and to take steps to mitigate these risks. The risk assessment should consider the kind of data that will be stored in the cloud, the security controls in place, and the potential impact of a security breach.
Compliance

Data security posture management also helps organizations to ensure compliance with regulatory requirements and industry standards. This helps organizations avoid potential fines and penalties associated with non-compliance. Organizations should ensure that the data stored in the cloud is compliant with industry standards, such as ISO 27001 and SOC 2, and with regulatory requirements, such as the California Consumer Privacy Act and the General Data Protection Regulation.
Secure Configuration
A secure configuration is critical to ensuring the safety of the cloud-stored data. Organizations should follow best practices for securing cloud infrastructures, such as using secure protocols and disabling unnecessary services and ports. In addition, organizations should regularly update and patch the cloud infrastructure to address any security vulnerabilities. Organizations should also implement network security controls such as firewalls and VPNs to ensure the security of the cloud-stored data.
Best Practices for Implementing Data Security Posture Management in Cloud Migration

Develop a Data Protection Plan
Organizations should develop a data protection plan that outlines the security measures that will be implemented to protect the data stored in the cloud. This plan should be reviewed and updated regularly to ensure that it remains relevant and effective.
Conduct a Thorough Risk Assessment
Organizations should conduct a thorough risk assessment to identify the potential risks associated with cloud migration. This assessment should consider the data stored in the cloud, the security controls in place, and the potential impact of a security breach.
Choose a Reputable Cloud Provider
Organizations should choose a reputable cloud provider with a strong track record of providing secure and reliable cloud services. Organizations should also review the security features and controls offered by the cloud provider and ensure that they meet their security requirements.
Implement Strong Access Controls
Organizations should implement strong access controls to prevent unauthorized access to the data stored in the cloud. This can include multi-factor authentication, role-based access controls, and access management policies.
Encrypt Data
Organizations should encrypt data at rest and in transit to protect the data stored in the cloud. This helps ensure unauthorized individuals cannot read the data, even if they gain access to it.
Monitor and Audit
Organizations should implement continuous monitoring and regular auditing to secure the data stored in the cloud. This includes monitoring for security incidents and auditing access to the data to ensure that the access controls are functioning properly.
Stay Up-to-Date with Security Updates
Organizations should stay up-to-date with security updates and patches to address any security vulnerabilities in the cloud infrastructure. This includes regularly updating the cloud infrastructure and applications to ensure they are secure.
Conclusion
Cloud migration can provide organizations with many benefits, such as scalability, cost-effectiveness, and agility. However, organizations must also consider the potential security risks associated with migrating to the cloud. Data security posture management is a critical component of cloud security that helps organizations to maintain a secure posture while using the cloud.
Data security posture management helps organizations mitigate the risks associated with cloud migration by ensuring that the data stored in the cloud is secure. Organizations can implement data security posture management by following best practices such as conducting risk assessment, choosing a reputable cloud provider, implementing strong access controls, encrypting data, monitoring and auditing, and staying up-to-date with security updates.