Traditional encryption and obfuscation methods are vulnerable to breaches due to the continually evolving threat landscape, revealing sensitive data through a collection of potential flaws known as cryptographic failures. In this article, you will learn about cryptographic failures and how to prevent them.
What are Cryptographic Failures?
When you do not adequately protect it, attackers frequently target sensitive data, including passwords, credit card numbers, and personal information. Sensitive data disclosure is primarily caused by cryptographic failure. Therefore, in 2021 the Online Web Application Security Project (OWASP) stated that it is now more crucial than ever to protect your data against cryptographic errors.
How to Prevent Cryptographic Failures
One can take several steps to ensure appsec in their SDLC to avoid cryptographic implementation flaws in contemporary applications. These include:
1. Use Authenticated Encryption Instead of Plain Encryption
While authenticated encryption upholds confidentiality and authenticity, plain encryption offers data confidentiality only. To ensure data privacy and authenticity, authenticated encryption employs the GCM (Galois Counter Mode) and CCM (Counter Mode with CBC MAC) block cipher modes.
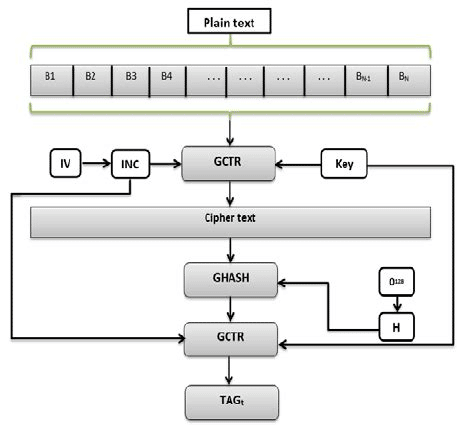
In addition, the protection against attack vectors provided by simultaneous data authenticity and confidentiality enforcement leaves little room for error when handling data in transit.
2. Enforce Key Rotation
Cryptographic attacks can be made against encryption keys, and the likelihood of an attack rises the longer a key is used. Attackers can use a security flaw in version control systems to continuously misuse the encryption key.
It is advised that developers use automated key creation and rotation to safeguard data against persistent breaches. To stop attackers from decrypting backups they created themselves, the process should also involve upgrading the keys, and re-encrypting protected content.
3. Catalog Data
Organizations must ensure that they maintain a careful check on all the data they save within the system to safeguard the clients’ data. Additionally, they ought to conduct recurring audits. This way, they will always be able to track owners, locations, security settings, and governance controls applied to the data being stored.
4. Assess Risks
Organizations must be aware of potential threats to the stored data to invest funds and resources to reduce such risks in a way that will assure data security. The likelihood that data will be harmed increases with its value. Even modest amounts of sensitive information can greatly impact the data subjects.
5. Discard Unused Data
It is impossible to compromise data that has been deleted. It is advised that developers make sure that apps immediately delete sensitive data if it is no longer needed. By substituting a non-sensitive placeholder for sensitive data, tokenization that complies with the PCI Data Security Standard can assist in discarding sensitive data. Truncation also obliterates a portion of important data, rendering it illegible.
6. Penetration Testing
One such area of security that is challenging to get completely right is cryptography. Therefore, you should perform routine penetration testing to ensure you haven’t overlooked anything. You can comprehend an attacker’s viewpoint of your program through penetration testing. Therefore, prioritizing fixes and finding any cryptographic and other weaknesses are easier when you think like an attacker.
7. Using TLS Encryption

Attackers may use this as an opening to access your network traffic. This goes beyond simply monitoring network traffic. Consider that a hacker may view all requests sent through your browser, alter requests, and take cookies from users’ active sessions. To gain access to data that has been encrypted, they can also force the connection from HTTPS to HTTP. Due to the exposure of very private and sensitive information, this might be fatal.
Conclusion
This is not an exhaustive analysis of all the ways that cryptography might go wrong, but it should help to clarify some of the common worries that web application developers will have as they attempt to make their apps secure.