Work is getting more convenient.
Bring Your Own Device (BYOD) Policies are becoming more common in offices.
Employees have the option of logging into their company’s network both from their homes and work.
However, the convenience of hybrid work, without suitable security policies and solutions, can create major security gaps.
Businesses today are acutely aware of this.
The problem is — as companies adapt their infrastructure to the cloud environment and make them more suitable for hybrid and remote work, the number of their security solutions grows with the scaling of networks and systems.
How can companies get back to basics and ensure that the complete infrastructure is covered while employees connect to the network from versatile devices?
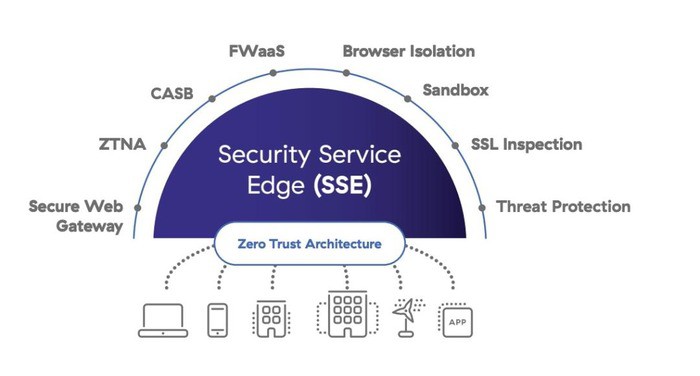
One security solution that combines all necessary cloud protection in a single platform is Security Service Edge (SSE).
SSE is an umbrella term for a wide range of security tools within one platform. This cloud-powered solution includes:
- Zero-Trust Network Access (ZTNA)
- Firewall as a Service (FWaaS)
- Secure Web Gateway (SWG)
- Cloud Access Security Broker (CASB)
How does SSE help you protect your most valuable assets during remote or hybrid work with these capabilities?
Let’s break down each functionality.
Zero-Trust Network Access (ZTNA)
ZTNA is the Security Service Edge component that enforces a so-called “zero trust” policy. This methodology is interpreted as trust but verified while others view it as trusting no one.
Instead of automatically assuming that every access attempt is genuine, it acknowledges that the hacker might have the credentials and use them to steal important documents. Or log into the network to deploy malware.
To protect sensitive data and prevent deep illicit access, only users with the right privileges can enter certain parts of the business network. That’s where role-based access comes in.
Within an application or a network, ZTNA triple-checks if the user is genuine when they try to access sensitive databases, log into a web application, or reach remote servers.
It analyzes if the activity matches the usual workflow of the employee. For instance, it could track the usual time they log in and sign off as well as which databases they normally access.
With these capabilities, ZTNA replaces the Virtual Private Networks (VPN) that many remote companies use to keep their work private.
Firewall as a Service (FWaaS)
Cloud-based FWaaS inspects incoming and outgoing traffic. It has similar capabilities to the traditional firewall. The main difference is that it applies them to the cloud environment instead of the physical one.
As a result, companies get firewall solutions that are more scalable and easier to deploy to the everchanging cloud technology.
Unlike traditional firewalls, FWssS can be applied to the network of multiple branch offices and data centers. It’s not restricted by the location of the office or even by the volume of the traffic.
One key capability of the FWaaS that increases the security of hybrid work environments is that it limits network access only to those who work for the company.
As with any other firewall, it can also automatically block the infected file from entering the private corporate network.
Secure Web Gateway (SWG)
Secure Web Gateway safeguards employees while they’re on the web. It prevents them from accidentally visiting phishing websites and installing malware on their devices. SWG can also detect infected files and stop the employee from downloading them to the machine.
Whether employees are working from home or office SWG will block access to unwanted websites — such as those that might contain viruses.
Sites that will be automatically blocked are those that don’t meet the security policies of the company, those that have been blacklisted, or that are known phishing sites.
Even employees who pass phishing awareness training can accidentally try to download malicious files from their email or a certain website. They might also try to open the link in an email that leads to a spoofed site. SWG prevents that from happening.
Cloud Access Security Broker (CASB)
CASB is integral for companies that are remote or hybrid while using many different types of Software as a Service (SaaS). It makes sure that security policies are enforced at all times those services are used.
The functionalities overlap with other Security Service Edge components on the list, but CASB implements them on the SaaS technology that the company uses every day.
That is, it regulates the access policies for SaaS devices, monitors the traffic, and enforces the zero-trust policy along with compliance policies that need to be met.
It prevents the SaaS that companies rely on from becoming a liability by ensuring that third-party solutions also match the security policies that the rest of the infrastructure adheres to.
As a result, remote companies have stronger cloud security all the while retaining visibility of the complete attack surface.
Protection on Both Technological and Human Levels
Security Service Edge (SSE) is a comprehensive tool for companies that shift to either fully remote or hybrid work. It simplifies security by providing all the necessary insights in one interface.
Every company is different. SSE allows them to customize many settings according to their security policies and unique work needs.
Besides having security tools such as SSE, it’s important to develop a culture of security and invest in security training for the general workforce.
What does that mean for security?
For cybersecurity, this means employees know that they can report if they notice something out of the ordinary — such as someone else using their computer or requesting to confirm the login request over the phone.
With phishing training awareness, they will also know common signs and scamming techniques that target employees while working both in the designated work office and homes.
To prevent hacking exploits that rely on human and technical errors, it’s important to have security that protects companies and employees from exploits that target them.