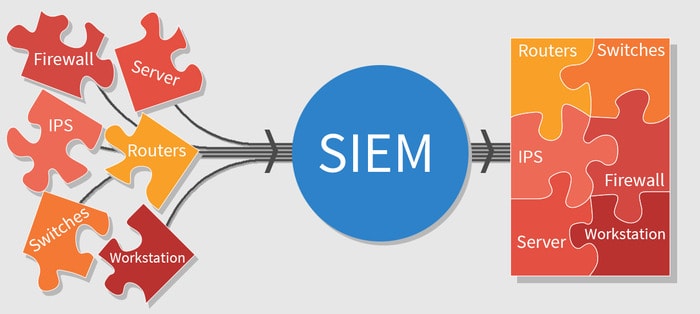
Within the computer system, a log is a computer-inclined or generated file that kind of captures an event or activity of what happened in an operating system or software. In security information and event management (SIEM), collecting, sorting, and storing these log files is incredibly important for it to achieve its purpose. Apparently, with the collection and processing of these log data, an SIEM solution can detect an anomaly and respond to any threat.
So, correctly undertaking the log management task can determine if an organization can detect and respond to threats effectively. But this can only happen with the proper practices and strategies. Thus, we have created an article that will act as a guide about SIEM logging, log management, and the best practices in implementing them.
Understanding Log Management, And Why It Is Important
Log management involves collecting, processing, storing, transmitting, analyzing, and synthesizing data logs from different devices and software. While exploring essential best practices in SIEM logging, log management aims to ensure data integrity, confidentiality, and availability to optimize system performance. Log management is extremely important in many organizations, but different tools work tirelessly to get things together.
In data collection, log management tools help collect data from several sources, such as operating systems, servers, software, and other user endpoints. Subsequently, other log management tools help in the analysis, indexing and search, retention, and reporting of the collected data.
Log management is crucial for organizations that want to maintain security or track real-time events. Most importantly, log management helps gather, sort, and store data in a centralized location. Since data plays a massive role in decision-making, log management helps the IT department get the data needed to make infrastructure health, resource distribution, and security decisions.
In log management, one of the major benefits is easy access to data, mainly from sorting /storing them in centralized locations. Furthermore, log management in next-gen SIEM solutions like Stellar Cyber helps improve security due to the real-time monitoring it offers. Not only does log management help detect and respond to threats, but it also helps enhance customer experience through predictive modeling and log data analysis.
Challenges Organizations Might Encounter From Log Management
Log management is filled with its own share of challenges, and some of them include:
-
Massive Data Volumes
In many organizations, there’s a massive production of data at an incredible rate, and it is often difficult to gather them. Furthermore, it also takes a lot of effort to collect and sort these large volumes of data, analyze, and store them. Thus, any log management solution must be designed to handle this large volume of data, or it would not effectively serve its function.
-
Data Format Standardization
In log management, one of the core functions is the collection of data from different sources, such as network devices, security devices, operating systems, IoT devices, and many others. One of the biggest challenges is putting these data in a single system while ensuring they follow the same standard format. However, having data logs in a standard format is very important; it helps security professionals to analyze data efficiently.
-
Presence of Latency
Between collecting data, sorting them, and storing them in a centralized location, a lot of latency occurs. In layman’s understanding, latency is simply the delay between when they take an action within a computer system and when they receive a response. When indexing a log file, there’s a massive latency at the time the data enters the log management system and the time it is included in search results.
-
Expensive and time-consuming
Especially when it is done manually by IT professionals, log management is an incredibly time-consuming process between gathering, indexing, analyzing, and storing data. Even when an organization tries to automate things by introducing AI and machine learning functionalities, these, too, can be incredibly expensive.
Strategies to Optimize Log Management for Enhanced Security
-
Automation Should Be a Priority
One of the things that will massively hinder the progress organizations make in their log management process is if they are doing it manually. Hence, they can introduce the automation of many events, such as collecting and analyzing data. When choosing SIEM and log management solutions, organizations should prioritize those with automation capabilities. An excellent example of SIEM logging tools with automation functionalities is those of Stellar Cyber.
-
Centralization over Decentralization
In log management, decentralization can hinder a lot of progress and prevent several security departments from having equal access to data. Storing, indexing, and connecting data in centralized locations ensures easy access and effectiveness in threat detection and response.
-
Log Collection Should be Done in the Right Way
Doing things wrong can incredibly limit many things in log management. Hence, data logs from different locations such as firewalls, servers, OS, applications, and users should be collected and stored correctly.
-
Investing in Cloud Tools and Resources for Scalability
Some log management solutions still store data collected in an in-house data storage system, which is outdated. Moreover, the ever-growing data landscape makes it very necessary for organizations to have scalable and flexible data storage systems. Apparently, organizations can only effectively and efficiently achieve this by investing in cloud tools. Depending on their needs, these cloud tools easily allow the organization to increase or decrease their data storage and processing capacity.
-
Data Retention Policy Should be In Place
The organization must be clear about certain things in log management, including its data retention policy. With the massive amount of data being produced daily, organizations should be transparent about the data they retain. Data retention for the long term is very important as it could help organizations meet their compliance requirements.
Conclusion
As a recap, log management is the collection, processing, transmitting, analyzing, and storing of data from different sources. Log management helps keep track of data produced by different users, devices, and applications within an IT infrastructure in real time. But for this to happen, organizations must abide by certain strategies or best practices. Some include automating data collection and analysis, centralizing data storage, investing in cloud tools and resources, and many others.
